Vulnerable Plugins
Ten disclosures this week, with three issues unfixed.
View this week's vulnerable plugin list.
The disclosure with the most visibility this week was in WooCommerce Product Vendors, where researchers from SiteLock discovered an unauthenticated, reflected Cross-Site Scripting vulnerability. Automattic was quick to patch the vulnerability and promptly released version 2.0.40. Also disclosed this week were PHP Object Injection vulnerabilities in the plugins JayJ Quicktag, VideoWhisper Live Streaming and WP Smart Security (currently unfixed). All three were discovered by researchers at pluginvulnerabilities.com. For the WP Smart Security vulnerability, they utilized the php-grinder.com service. PHP-Grinder is a static analysis tool designed specially to scan WordPress plugins and PHP-based GitHub projects for potential security vulnerabilities. If you're new to static analysis, this is a great introduction to see how static analysis works. In looking at the report for WP Smart Security, we can see it identified a potentially insecure use of unserialize on line 20 of secure.php. Looking at the source we find unserialize is being called on the contents of $HTTP_RAW_POST_DATA after being base64 decoded, which is definitely of concern.
I was fortunate to use the initial 0.1 beta of php-grinder.com and have been extremely happy with the 0.2 version. I would encourage you to test out your own plugins/projects for issues. If you decide to test any plugins that you use, and you do find a vulnerability, please be sure to communicate immediately with the author. If they are unresponsive, report the vulnerability to plugins@wordpress.org following their guidelines.
Security PSAs
If you haven't already implemented ssl on your site, you're most likely going to be flagged as "Not Secure" in Chrome starting in October. Starting with Chrome version 62 (slated for an October 24th release), pages that contain an input element that are not served over https will be marked as "Not Secure", and for all non-https pages when Chrome is in incognito mode, according to an email from Google sent to site owners earlier this month.Google has been using https as a light search ranking signal for several years; this is simply the next step in Google's effort to increase SSL adoption across the web.

While I applaud their attempt to motivate site owners to secure communications between the web server and the end-user, I fear this step, while well intentioned will makes things worse. Unfortunately, many people have come to associate the lock+"Secure" in the browser to mean the site they are visiting is "safe". And while the connection between the server and the browser will be "safe", it doesn't help the end user if the server/site on the other end is compromised, or actively trying to exploit the user. In addition, given Let's Encrypt's less than stellar record in issuing certs to phishing domains, and that their certs are only domain validation certificates, not identity verification certificates, we end up with a precarious situation. Do you think the average user will know the website on the right is a phishing site?
[caption id="" align="aligncenter" width="848"]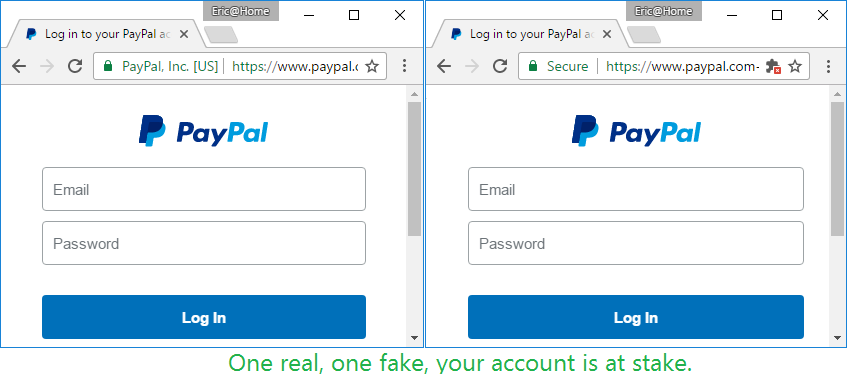 Credit Scott Helme[/caption]
Credit Scott Helme[/caption]
In either case, if your site is not currently being served over https, and it contains any input elements (like a search field) just know that starting at the end of October, you'll probably start receiving communications from users concerned that your site has been compromised.
Second, Proofpoint recently revealed they've been tracking a ransomware strained they've dubbed Defray that is targeting the Healthcare and Education industries in the US and UK. Distribution is typically via email with a Word document attachment. The Word document has what is supposed to look like an embedded YouTube video, but is actually an embedded executable. As always, be skeptical of any emails you receive unexpectedly that contain attachments.